Prompt Templates for Pro-level test cases
Get prompt-engineered templates that turn requirements into structured test cases, edge cases, and negatives fast every time.
TL;DR:
What MFA testing is: A process to validate if MFA mechanisms are correctly and securely implemented.
Why it’s important: It prevents a false sense of security and protects against real-world threats like MFA fatigue and social engineering.
Key components: The three main areas to test – authentication factors, environments, and user journeys.
MFA testing is a cornerstone of modern security assurance, not just a one-time setup. It highlights the proactive nature of testing to ensure authentication is not just present, but truly resilient against evolving threats.
Cyberattacks are getting more sophisticated by the day, and stolen credentials remain one of the top causes of data breaches. While Multi-Factor Authentication (MFA) has become the gold standard for securing logins, simply deploying MFA isn’t enough.
If it isn’t thoroughly tested, organizations risk leaving open backdoors for attackers to exploit.
That’s where MFA testing comes in: verifying that authentication flows work consistently, securely, and with minimal friction for end users.
This guide covers everything you need to know about MFA testing: what it is, why it matters, how to do it effectively, and what the future holds.
Table Of Contents
- 1 What is MFA testing?
- 2 Why MFA testing matters in security assurance?
- 3 3 key components of MFA testing
- 4 How to perform MFA testing? (step-by-step guide)
- 5 Challenges in MFA testing and how to overcome them
- 6 Best practices for effective MFA testing
- 7 MFA testing vs. other security testing methods
- 8 The future of MFA testing
- 9 Strengthening security with robust MFA testing
- 10 FAQS on MFA testing
What is Mfa Testing?
Multi-Factor Authentication (MFA) requires users to provide two or more forms of verification before granting access to a system.
It adds an extra layer of security by combining factors like passwords, OTPs, or biometrics, making it harder for attackers to break in with stolen credentials alone.
MFA testing is the process of validating whether these authentication mechanisms are implemented correctly, securely, and reliably across different platforms and user scenarios.
Important: Implementation is about setting up the authentication methods, while testing ensures those methods actually work as expected under real-world conditions: whether that’s on a mobile device, in a cloud environment, or during password recovery.
With cyberattacks exploiting weak or inconsistent authentication, testing MFA is no longer optional: it’s essential.
Why Mfa Testing Matters in Security Assurance?
Organizations may roll out MFA with the best intentions, yet gaps in configuration, usability, or reliability can weaken its effectiveness. Security assurance means not just trusting the setup; it means validating it.
Without structured testing, MFA can create a false sense of security. A system might appear locked down but still be vulnerable if codes fail to arrive on time, if push approvals can be tricked, or if recovery options open backdoors for attackers. In other words, the risks don’t disappear after implementation; they simply shift.
This is why MFA testing is essential: it transforms MFA from a theoretical safeguard into a proven defense against real-world threats.
Poorly implemented MFA can lead to:
- OTP codes delivered late or not at all.
- Push notifications going to the wrong device.
- Biometrics failed due to device inconsistencies.
- Users bypass MFA through misconfigurations.
Real-world breaches have shown this risk. For example, the 2022 Uber breach demonstrated how attackers exploited MFA fatigue by bombarding an employee with push notifications until one was approved.
According to Verizon’s Data Breach Investigations Report, stolen credentials are still the most common attack vector, despite widespread MFA adoption.
Testing MFA workflows is just as important as deploying them. It ensures attackers can’t exploit loopholes and that users won’t be locked out due to poorly designed flows.
Sample Scenarios
To ensure MFA works reliably across different factors, devices, and user flows, it’s helpful to define clear test scenarios.
| Test scenario | Objective | Expected result | Type |
| Login with credentials + OTP | Verify successful authentication | Access granted | Positive |
| Login with incorrect OTP | Verify system blocks invalid codes | Access denied | Negative |
| OTP delivery via SMS | Ensure OTP is received | OTP delivered on time | Functional |
| Biometric login | Validate fingerprint/facial recognition | Access granted for registered user | Functional |
| Password recovery with MFA | Test recovery flow | Password reset successful | Edge case |
Well-rounded MFA testing confirms that security layers hold up without creating friction for genuine users.
3 Key Components of Mfa Testing
To test MFA effectively, you need to look beyond just checking whether a code or biometric works. Authentication flows touch different devices, environments, and user scenarios: each of which can introduce unique risks.
If these areas aren’t tested thoroughly, attackers may exploit the weak spots or users may face frustrating login failures.
That’s why MFA testing is best approached as a multi-layered process. It covers not only the authentication factors themselves, but also the platforms where they’re used and the user journeys that tie them together.
Let’s break these components down:
1) Authentication Factors to Verify
When testing MFA, it’s important to validate each factor independently, since attackers often target the weakest link. A thorough check ensures security without frustrating users.
- Something you know: Passwords, PINs, secret questions.
- Something you have: OTPs via SMS/email, hardware tokens, authenticator apps, mobile push notifications.
- Something you are: Biometrics such as fingerprints, facial scans, or voice recognition.
Each factor must be tested for reliability, security, and fallback options in case of failure.
2) Environments and Contexts
Tests must cover every environment where users log in. This ensures consistency and avoids gaps that hackers could exploit.
- Web apps: Browser-based login flows.
- Mobile apps: Native app authentication, biometric integrations.
- Cloud/SaaS platforms: Access to services like AWS, Salesforce, or Office 365.
Testing should confirm MFA works across all environments where users interact with your system.
3) User Journeys & Edge Cases
Users encounter MFA at multiple touchpoints. Covering real-world cases helps you balance strong security with a smooth user experience.
- Standard login
- Password reset and account recovery
- Switching devices
- Offline or poor-network scenarios
Covering these journeys ensures MFA is not only secure but also user-friendly.
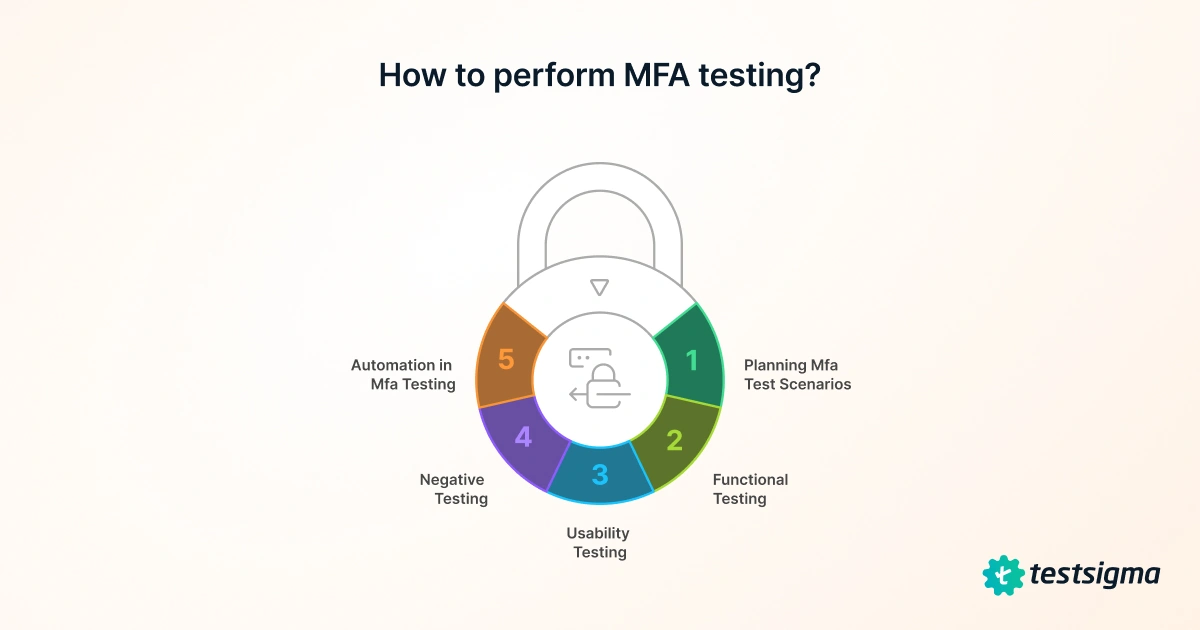
How to Perform Mfa Testing? (step-by-step Guide)
Knowing what to test is only half the battle: the real challenge lies in executing those tests in a structured and repeatable way. MFA touches multiple systems, involves external services like SMS or email gateways, and often requires users to juggle between devices.
Here’s a sample framework:
Manual MFA Testing Workflow
Plan test scenarios → Execute OTP/biometric tests → Check edge cases → Document results → Report issues
Automated MFA Testing Workflow
Configure automation scripts → Simulate OTPs/push notifications → Run regression tests → Validate results → Log findings → Continuous integration
Without a clear framework, testing can quickly become inconsistent or incomplete.
As quoted by a TestSigma expert:
“MFA testing is not just about verifying codes or biometrics; it’s about ensuring every authentication flow is reliable, secure, and user-friendly. Automating these tests wherever possible can save time while maintaining high security standards.”
Now, let’s go through a step-by-step guide that teams can use as a practical blueprint for MFA testing:
Step 1: Planning Mfa Test Scenarios
- Define acceptance criteria aligned with security policies.
- Identify supported authentication factors.
- Determine risk-based use cases (e.g., high-value transactions requiring stronger MFA).
Step 2: Functional Testing
- Validate OTP delivery via SMS, email, or apps.
- Test mobile push notifications across iOS and Android.
- Verify biometric recognition across supported devices.
- Confirm fallback methods when primary MFA fails.
Step 3: Usability Testing
- Ensure MFA doesn’t introduce excessive friction.
- Check for accessibility (screen readers, large font support).
- Validate clear instructions for less tech-savvy users.
Step 4: Negative Testing
- Enter expired or incorrect OTPs.
- Attempt replay attacks.
- Test MFA bypass attempts (e.g., device cloning).
This is where many hidden vulnerabilities come to light.
Step 5: Automation in Mfa Testing
While manual testing is critical, automation can streamline repetitive checks:
- Automate OTP validation for functional regression.
- Use tools like Testsigma to simulate MFA workflows across devices.
- Mock SMS/email gateways to test delivery without incurring real costs.
Automation won’t replace human judgment, but it can speed up consistency checks dramatically.
Challenges in Mfa Testing and How to Overcome Them
On paper, MFA may look straightforward: enter a password, confirm a code, and you’re in.
But when it comes to testing: tokens expire within seconds, authentication flows often span multiple devices, and external services like SMS or email gateways can introduce delays or failures.
Add in the complexity of automating biometric or CAPTCHA-based steps, and it’s clear that MFA testing brings its own set of hurdles.
Recognizing these challenges upfront is the first step to building a reliable testing strategy.
Let’s look at the most common issues teams face, and how to work around them effectively:
- Time-sensitive tokens: OTPs expire in seconds, making automation tricky.
Solution → Use clock synchronization and token mocking. - Network delays: SMS delivery may lag.
Solution → Simulate low-bandwidth and high-latency environments. - Cross-device testing: MFA often requires switching between laptop and mobile.
Solution → Use device farms or emulators. - External dependencies: Reliance on SMS/email gateways.
Solution → Mock external services for stable testing. - Automation challenges: Captchas and biometric verification resist automation.
Solution → Use real-device testing labs to cover these scenarios.
Best Practices for Effective Mfa Testing
True security assurance comes from following consistent practices that strengthen every test cycle. Here are some best practices to ensure that MFA isn’t just functioning, but also resilient, user-friendly, and adaptable to future risks.
To get the most out of MFA testing, follow these principles:
- Simulate real-world conditions (slow networks, poor connectivity).
- Cover positive and negative cases (successful logins, failed attempts).
- Test accessibility (voice prompts, alt-text, inclusive biometric options).
- Run regression tests regularly, especially when integrating new factors.
- Document fallback policies so users aren’t locked out completely.
Mfa Testing Vs. Other Security Testing Methods
MFA testing doesn’t exist in isolation; it complements other forms of security testing.
To understand its unique role, here’s a quick comparison:
| Testing method | Primary focus | Relation to MFA | Key takeaway |
| Penetration testing | Identifies and exploits vulnerabilities in systems, apps, or networks. | Includes attempts to bypass or break MFA protections. | Pen testing validates MFA strength from an attacker’s perspective. |
| SSO testing | Ensures single sign-on works seamlessly across apps and services. | Often combined with MFA to add extra login security. | SSO testing checks convenience, while MFA testing checks robustness. |
| 2FA testing | Validates use of exactly two authentication factors | A narrower form of MFA testing. | MFA testing is broad covering multiple layers and factor combinations. |
| MFA testing | Verifies that multiple authentication factors are implemented correctly, securely, and reliably. | Stands as its own layer of assurance beyond other methods. | A cornerstone of holistic security, ensuring authentication truly protects against threats. |
MFA testing is broader: it validates multiple authentication layers, making it a key piece of an overall security strategy.
The Future of Mfa Testing
Authentication is no longer just about verifying identity: it’s about staying ahead of attackers who are constantly adapting their methods.
As organizations shift toward passwordless logins, adaptive security, and AI-driven monitoring, MFA testing will need to evolve alongside these innovations.
Testing strategies must expand beyond today’s OTPs and biometrics to cover new authentication models and emerging risks.
As cyber threats evolve, MFA testing must keep pace. Some key trends shaping the future include:
- Passwordless authentication: Using biometrics and hardware keys.
- Adaptive authentication: Context-aware MFA that adjusts based on device, location, or user risk.
- AI-driven threat detection: Monitoring login anomalies and suspicious MFA requests in real time.
Testing will need to expand into these areas to ensure future-proof security.
Strengthening Security with Robust Mfa Testing
Deploying MFA is a step in the right direction, but it’s only half the battle. Without structured testing, even the strongest MFA systems can fail at critical moments.
By planning scenarios, covering functional and negative cases, simulating real-world conditions, and using automation wisely, organizations can ensure their MFA systems are both secure and user-friendly.
To keep MFA reliable without slowing releases, consider a no-code tool that automates the whole flow – OTP delivery, validation, fallbacks, and cross-browser/mobile checks.
With Testsigma you can automate MFA tests and add them to your regression suite in minutes, so security stays strong as you ship faster.
FAQs on Mfa Testing
MFA testing verifies that multi-factor authentication works correctly and securely across devices, platforms, and scenarios, ensuring that passwords, OTPs, push notifications, and biometrics function reliably without causing user friction.
Test OTPs by checking timely delivery, expiration, rejection of incorrect or replayed codes, and fallback options. Both real-device testing and automation help ensure OTPs are secure and consistently functional.
Yes, weak implementation can allow bypass through MFA fatigue, SIM swaps, or misconfigured recovery flows. Proper MFA testing identifies and fixes such vulnerabilities before attackers exploit them.
Challenges include time-sensitive tokens, network delays, multi-device testing, and automating biometrics or captchas. Mocking services and device farms help overcome these issues.
2FA uses exactly two factors, while MFA testing covers multiple factors and combinations. MFA testing ensures layered authentication works securely across all scenarios, not just a simple two-step process.



