Prompt Templates for Pro-level test cases
Get prompt-engineered templates that turn requirements into structured test cases, edge cases, and negatives fast every time.
Sandboxing is a vast concept used in a variety of domains, from children’s toys to computer security. This term originates from creating a box of sand for children who do not go along together very well. By this method, they create a boundary or their own space in which they can play and not interfere with one another. Today, whenever we want to create a concept where two entities need to be separated in such a way that the working of one does not interfere with the working of the other, we name it a sandbox.
Table Of Contents
- 1 What is Browser Sandbox?
- 2 Why is Browser Sandboxing Essential?
- 3 Types of Browser Sandboxing
- 4 Pixel Streaming
- 5 DOM Mirroring
- 6 Sandboxing in Major Browsers
- 7 Safari Sandbox Architecture
- 8 How to Disable Browser Sandbox (and Why Not To)
- 9 Use Cases and Applications of Browser Sandbox
- 10 Challenges and Limitations of Browser Sandboxing
- 11 Conclusion
- 12 Frequently Asked Questions
What is Browser Sandbox?
A browser sandbox is a security mechanism that isolates the browser’s execution processes, such as rendering web pages, running scripts, or downloading files from the underlying operating system and local resources. In simpler terms, it creates a protective “box” around browser activity so that even if malicious content is encountered, it cannot freely breach your system. Rather than being a user-facing feature, browser sandboxing is entirely a security measure: it restricts what the browser (and code running within it) is allowed to do.
Why is Browser Sandboxing Essential?
Browser sandboxing is crucial because modern web browsers are the frontline target for cyberattacks. Every time you open a website, click a link, or download a file, the browser executes code that could be harmless or malicious. Without isolation, any exploit inside the browser could directly access your operating system, files, and even network.
Key Reasons for Isolating Browser Activity
- Frequent Target for Attacks
Browsers interact with untrusted websites daily, making them a high-risk entry point for malware, phishing, and zero-day exploits. By sandboxing, suspicious code is restricted to a contained environment. - Defense Against Multiple Threat Vectors
- Malware downloads that try to install on your device
- Malicious scripts hidden in web pages
- Phishing attacks that exploit browser vulnerabilities
- Zero-day exploits targeting browser engines
With sandboxing, these threats stay isolated and cannot freely harm the system.
- Protects Critical Resources
Even if a browser process is compromised, sandboxing prevents it from easily accessing sensitive files, applications, or networked systems effectively containing the damage. - Enables Safe Testing Environments
For developers, QA engineers, and security researchers, browser sandboxes provide a safe environment to test new features, run automation, or simulate attacks without endangering production systems.
Types of Browser Sandboxing
Not all sandboxing strategies work the same way browsers and organizations adopt different models depending on performance, security, and use cases. The two main approaches are:
1. Local Sandbox Isolation
In this model, the browser runs directly on your device but inside a restricted environment.
- Each tab, plugin, or process is compartmentalized.
- Even if one tab is compromised by malware, it can’t easily access your files or system-level resources.
- Popular browsers like Chrome and Edge rely on process-level sandboxing for everyday protection.
2. Remote (or Cloud) Sandbox Isolation
Here, the browser itself doesn’t actually run on your machine. Instead:
- The browsing session happens on a remote server, and only a visual stream of the page is sent to your device.
- Any malicious scripts or attacks execute remotely, keeping your system untouched.
- This approach is increasingly popular in enterprise setups where secure, large-scale browsing and testing are required.
Pixel Streaming
Pixel streaming is a secure content delivery method where the entire browsing session is executed on a remote server, and only the visual output (pixels) is streamed to the user’s device. This means the local system never directly processes the underlying code, scripts, or files from the visited website.
- Malicious scripts or drive-by downloads can’t execute locally since the browser engine never runs on the user’s device.
- High-security enterprise environments, cloud-based browser isolation, and situations where full separation from web threats is needed.
DOM Mirroring
DOM mirroring takes a hybrid approach: the browser’s Document Object Model (DOM) structure is replicated on the user’s device, but all risky operations like running JavaScript are handled remotely.
- Users see and interact with web content in real time, but the actual execution occurs in a safe, isolated environment.
- Faster performance and smoother user experience compared to full pixel streaming, while still maintaining strong security controls.
Sandboxing in Major Browsers
Different browsers implement sandboxing in unique ways, balancing performance, usability, and protection. Here’s how the browsers approach it:
Chromium Browser Sandbox
Chromium-based browsers (Google Chrome, Microsoft Edge, Brave, etc.) use a multi-process sandbox model,
- Broker and Target Processes:
- Target process (e.g., rendering a webpage or executing JavaScript) runs with restricted privileges.
- Broker process acts as a gatekeeper, deciding what limited actions the target can perform outside the sandbox.
- File access, network requests, and device calls are tightly regulated.
- You can see Chromium’s sandboxing in action via the chrome://sandbox page, which outlines enabled security layers.
This ensures that even if one tab or extension is compromised, it cannot freely affect the system or other browser processes.
Firefox Sandbox
Mozilla Firefox follows a parent-child process architecture with configurable sandbox levels
- Parent process manages UI, permissions, and system interactions.
- Child processes handle risky tasks like rendering, content scripts, or media playback, but operate in restricted environments.
- Firefox allows different degrees of restriction from low isolation for compatibility to higher levels for tighter security.
- Advanced users can tweak sandboxing behavior via about:config settings such as security.sandbox.content.level.
This model helps balance security with performance, especially across different OS environments.
Microsoft Edge Sandbox
Microsoft Edge, while Chromium-based, also includes Windows-integrated sandbox features:
- Built-in integration with Windows Defender Application Guard (WDAG) for enterprise users.
- Ability to open suspicious websites in a completely isolated container separate from the host OS.
- Isolation Experience: When browsing in an Application Guard session, Edge runs in a dedicated sandbox environment.
- Once the sandbox session is closed, all browsing history, cookies, and downloaded files within that environment are automatically discarded ensuring no residual risk.
- Users can enable WDAG via Windows security settings or Group Policy.
This makes Edge a strong choice for enterprises prioritizing high-assurance browsing security.
Safari Sandbox Architecture
Apple’s Safari browser relies on the macOS and iOS security frameworks to enforce sandboxing. Its design emphasizes system-level integration and restrictive defaults.
- Process Isolation: Each webpage or tab runs in a separate process, confined within a sandbox that limits access to files, system resources, and sensitive APIs.
- System Integration: Safari leverages macOS App Sandbox and iOS application sandboxing. These restrict browser processes from performing unapproved actions like accessing the file system, camera, or microphone without explicit user consent.
- JIT Hardening: Safari applies sandboxing to JavaScript’s Just-In-Time (JIT) compiler, reducing potential exploits.
- Security Focus: Because Apple tightly controls both hardware and software, Safari sandboxing is optimized for iPhones, iPads, and Macs ensuring minimal attack surface while preserving performance.
This architecture makes Safari particularly strong in mobile environments, where strict sandboxing helps balance usability with robust protection.
How to Disable Browser Sandbox (and Why Not to)
While most of us would not want to work with a browser that is not secure and can harm our data, a few can raise the question of whether we can disable the sandbox in the browser.
There are no generalized scenarios for such a requirement. However, I can recall my personal experience where the below-described methods were used to disable the sandbox in a browser.
- There are a few people who are in sandbox development as a combined open-source project or personal project. They require to disable the browser and verify the working of their own sandbox.
- There are a few people who may want to use a third-party browser sandbox due to any reason.
- Linux systems may prohibit using a browser sandbox due to security policy clashes at the root user level. The browser could only be operated when the browser sandbox is disabled in such cases.
When we are in such a situation, although it is strongly advised never to disable the sandbox, we may have to do so. Let’s see what options a browser provides to disable sandbox. May be needed, it’s almost never recommended for everyday browsing.
Disabling Sandbox in Chromium Browsers
To disable the sandbox in chromium browsers such as Google Chrome, execute the following steps:
- Go to the shortcut icon of the browser and right-click on it.
- Select Properties.
- Type “–no-sandbox” after the path written in front of the Target box.
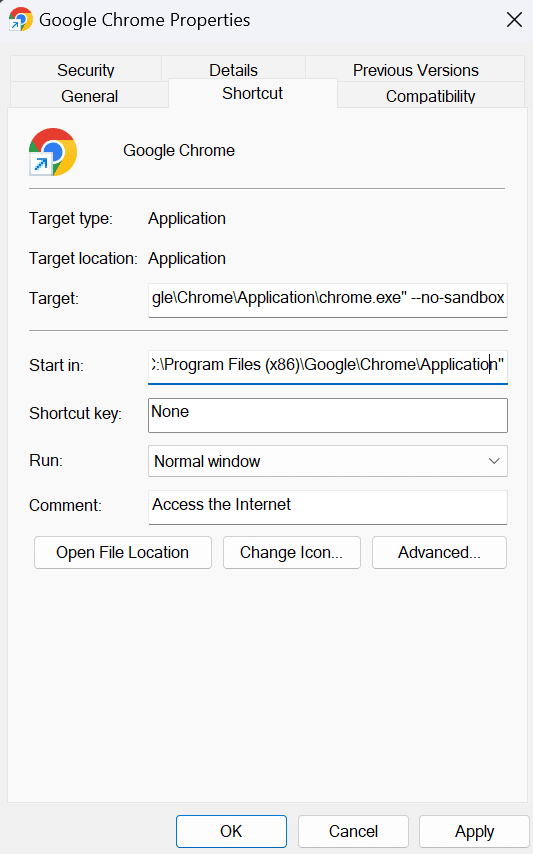
4. Close and reopen the browser with the applied effect.
Disabling Sandbox in Mozilla Firefox
Mozilla’s Firefox browser works according to the set environment variables in the system. A lot of them correspond to the sandbox feature, also. So unlike what we did in the Chromium browser, here you can select which part of the sandbox you would like to disable.
- Locate the firefox.exe file as it is the directory where you have installed the Firefox browser.
- Open the command prompt in this location.
- Alternatively, you can also open the command prompt in any location and change the directory to the firefox.exe location.
- Now here, you can set the DISABLE sandbox variables to 1 where you don’t need any.
For instance, if the content sandbox needs to be disabled, then: set MOZ_DISABLE_CONTENT_SANDBOX = 1You can find the list of all the environment variables in Firefox.
Disable Sandbox in Safari Browser
Currently, disabling the sandbox in the Safari browser is not allowed due to security reasons.
Use Cases and Applications of Browser Sandbox
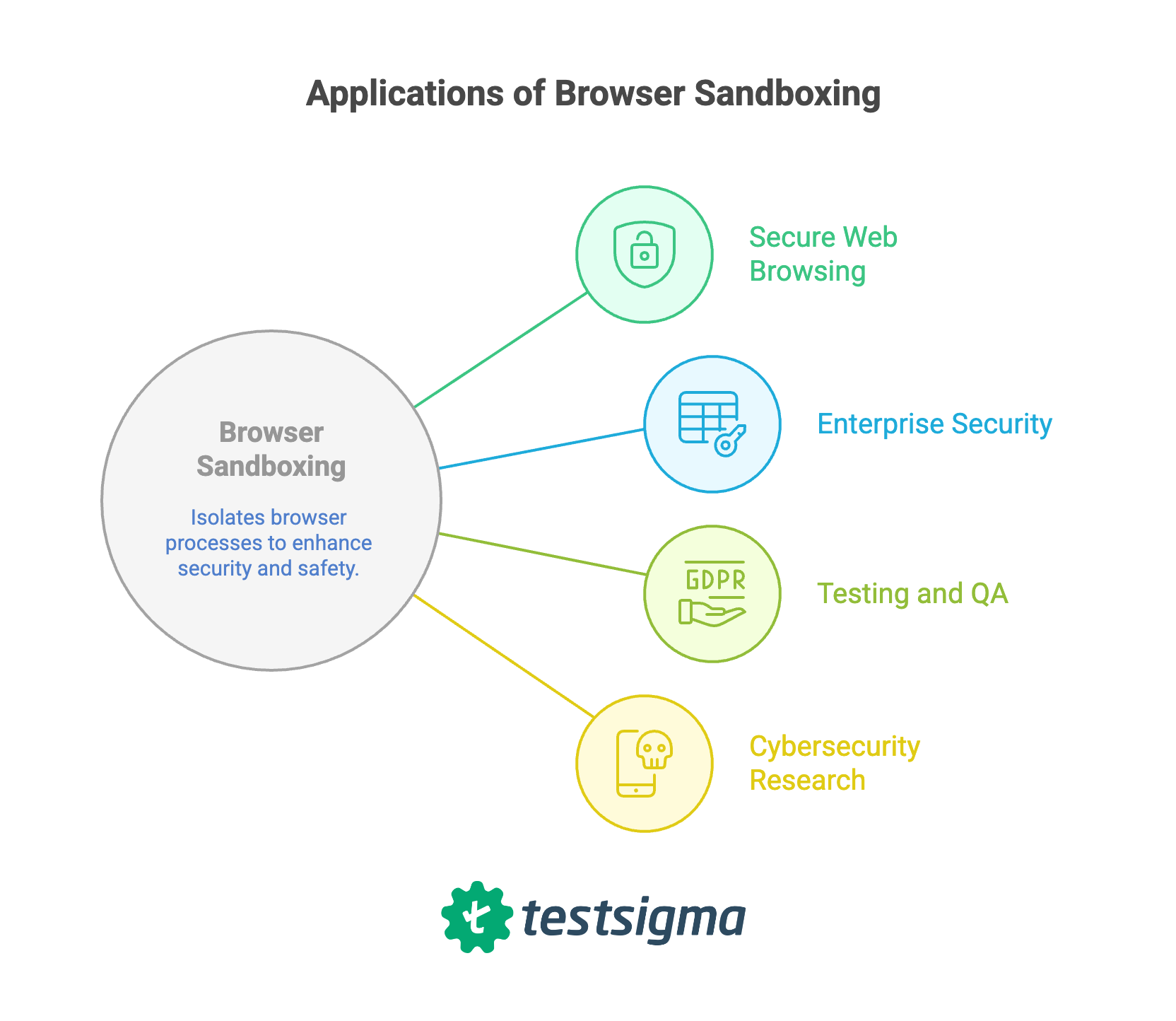
- Secure Web Browsing – Everyday users benefit from sandboxing because it isolates malicious scripts, phishing attempts, and harmful downloads from compromising the system.
- Enterprise Security – Organizations use sandboxed browsers, often with remote isolation to protect sensitive data, enforce compliance, and mitigate insider or external threats.
- Testing and QA – Developers and QA teams run applications in sandboxed browsers to test new features or debug code safely, without risking production environments.
- Cybersecurity Research – Security professionals use sandboxed browsers to safely analyze malware, simulate attacks, and study exploits.
Challenges and Limitations of Browser Sandboxing
- Performance Overheads – Multiple isolated processes or remote streaming may consume more memory and CPU, especially on resource-limited devices.
- Compatibility Issues – Some advanced web apps, browser extensions, or plugins may not function properly within strict sandbox restrictions, limiting usability.
- Not Foolproof – Sophisticated zero-day exploits, kernel-level vulnerabilities, or privilege-escalation attacks can sometimes escape the sandbox.
- User Experience Trade-Offs – Approaches like pixel streaming may reduce interactivity, add latency, or impact visual quality compared to direct rendering.
- Increased Resource Management Complexity – For IT teams, managing sandbox policies, updates, and isolation configurations across devices can introduce administrative overhead.
- Limited Offline Functionality – Some sandboxed browsers or remote isolation strategies rely heavily on cloud infrastructure, reducing usability in offline or low-connectivity environments.
- Device and OS Dependency – Sandbox effectiveness often depends on the underlying operating system’s security model (e.g., Windows vs. macOS vs. Linux), meaning protections may vary across platforms.
- Potential False Sense of Security – Users may assume sandboxing makes them invulnerable and ignore other best practices like patching, secure browsing habits, and endpoint protection.
Conclusion
Browser sandboxing has become a cornerstone of modern web security. By isolating browsing activity, it dramatically reduces the risks posed by malware, phishing, and untrusted web content. While not without its limitations, such as performance costs or compatibility hurdles it provides a critical safety net that balances security with usability.
For individuals, sandboxing ensures safer day-to-day browsing. For organizations, it delivers enterprise-grade protection and secure testing environments. Ultimately, the message is clear, keep sandboxing enabled and rely on it as one of the most effective defenses in the evolving landscape of web threats.
Frequently Asked Questions
A browser sandbox isolates web activity, such as loading pages, running scripts, or downloading files from your operating system. Its primary purpose is to contain potential threats like malware or malicious scripts so they cannot spread to your files, applications, or network.
While some users may try to disable sandboxing to reduce memory usage or troubleshoot issues, it’s not recommended. Disabling removes a critical security layer, leaving your device vulnerable to malware, phishing, and zero-day exploits. It should only be done in controlled environments like debugging or research labs.
No. While browser sandboxing significantly reduces risk, advanced attacks, such as privilege-escalation exploits or kernel-level vulnerabilities may still bypass it. That’s why sandboxing works best when combined with other security practices like regular updates, endpoint protection, and cautious browsing habits.



